Software Bill of Materials: What to Know About SBOMs for Medical Devices
On May 12, 2021, President Biden signed the Executive Order On Improving the Nation’s Cybersecurity. Among other items in the executive order was a requirement that every vendor that supplies the federal government with software must provide a software bill of materials (SBOM) with their product.
Given that the federal government spends nearly $100 billion a year on IT services, the executive order has put a spotlight on the concept of an SBOM and cybersecurity in general.
Nowhere are these issues more pressing than in the medical device industry, where lives depend on the development of safe and secure software. So today, let’s take a look at the SBOM and the role it plays in medical device manufacturing and cybersecurity.
What is a software bill of materials (SBOM)?
The National Telecommunications and Information Administration (NTIA) describes an SBOM as “a formal, machine-readable inventory of software components and dependencies, information about those components, and their hierarchical relationships.”
In practice, that means an SBOM is a detailed list of all the components used in a given software application. Typically, this is a mix of proprietary and open-source code, and your SBOM should include the licenses, versions, and vulnerabilities of any open-source code you use.
President Biden’s executive order also directed the NTIA to create a list, which it now requires from software suppliers, of the minimum required elements the government expects in the SBOMs. The minimum required elements fall into three categories:
-
Data Fields - These contain the basic information that should be tracked and maintained for each component.
-
Automation Support - Organizations need to provide automation support to ensure that the data on SBOM components can be generated and read across organizations.
-
Practices and Processes - These are the elements that must be addressed in order to integrate the SBOM into an organization’s development lifecycle. Basically, they answer the questions of how and when to update and deliver the SBOM.
| NOTE: You’ve probably also seen “software bill of materials” used interchangeably with “cybersecurity bill of materials” (CBOM). However, an SBOM and a CBOM are not the same thing. A CBOM is a list of both the software and hardware vulnerabilities in a product, while an SBOM refers strictly to software. |
Why do medical device manufacturers need a software bill of materials?
The number of medical devices that will need an SBOM—because they use software or they are software—is increasing at a rapid clip. Software as medical device (SaMD) is one of the fastest growing categories of medical devices, and many devices that used to be standalone are now network connected.
That surge in connected medical devices is coinciding with a dramatic increase in the number of cyberattacks in the healthcare sector. Forbes reports that the number of hacking incidents in healthcare increased by 42% in 2020, and the industry is consistently one of the top targets for criminals looking for patient data, opportunities for ransoms, or both.
This isn’t just a hospital IT problem, either. New vulnerabilities in software are being discovered all the time, and older medical devices are particularly susceptible to these problems. For an idea of how one weakness can have a cascading effect, look no further than the recent discovery of critical vulnerabilities in Siemens software. Millions of medical devices were affected because they all used the same code.
An SBOM helps to improve your device’s cybersecurity two ways:
-
First, compiling an SBOM helps ensure that medical device manufacturers identify vulnerabilities as they build their product and then identify the risks that stem from those vulnerabilities. Once you understand the risks, you can put controls in place to mitigate them or avoid them entirely.
-
Second, when a vulnerability is identified while a product is on the market, having a thoroughly documented SBOM ensures that manufacturers know exactly which products are affected and accelerates the timeline for addressing the issue.
You have to know there’s a problem before you can fix it, and a software bill of materials is one of the most powerful tools in your arsenal for identifying and avoiding potential problems in your code.
What is the latest FDA guidance on SBOMs?
The Food and Drug Administration is not sitting idly by as these cybersecurity risks continue to grow. Back in 2018, the agency drafted guidance on what medical device manufacturers should include in their premarket submissions if their devices have cybersecurity risk.
Today, FDA officials are becoming increasingly vocal about the need for strong cybersecurity measures for medical devices, and they expect medical device manufacturers to take the threat of cyber attacks seriously. In fact, Kevin Fu, the acting director of medical device cybersecurity at the Center for Devices and Radiological Health, has openly stated that “FDA has denied premarket clearance based solely on cybersecurity concerns for medical devices.”
And while providing FDA with an SBOM is technically a voluntary act at the moment, FDA is currently pushing to make SBOMs a requirement for premarket submissions. The agency would also like to require manufacturers to show they’re capable of updating and patching security in their products in their premarket submission. Postmarket requirements for coordinated disclosure of cybersecurity vulnerabilities are also on the FDA’s wish list.
The agency will need Congressional action to grant it some of these powers, but President Biden’s executive order has shown there is plenty of appetite for cybersecurity measures right now. Manufacturers that build SaMD or connected devices would be wise to read the writing on the wall when it comes to SBOMs and cybersecurity for their devices.
For now, you can reference this complete list of the FDA’s current cybersecurity guidance to get a better sense of exactly what is expected for your particular device.
Make cybersecurity an integral part your medical device’s design with Greenlight Guru
With the FDA’s aggressive stance on SBOMs for medical devices, it’s more important than ever that you can document both the cybersecurity risks for your device and the controls you use to mitigate them.
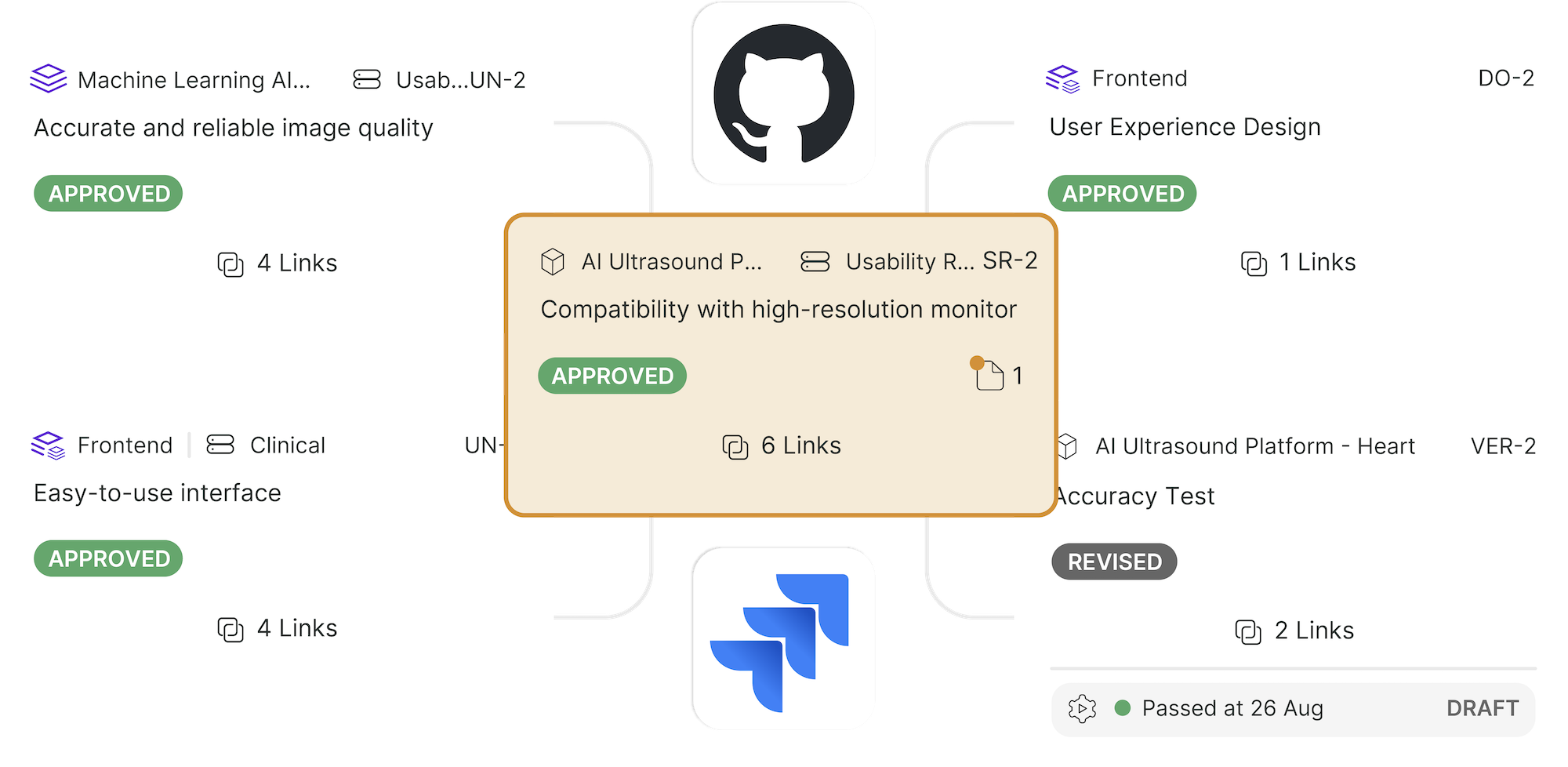
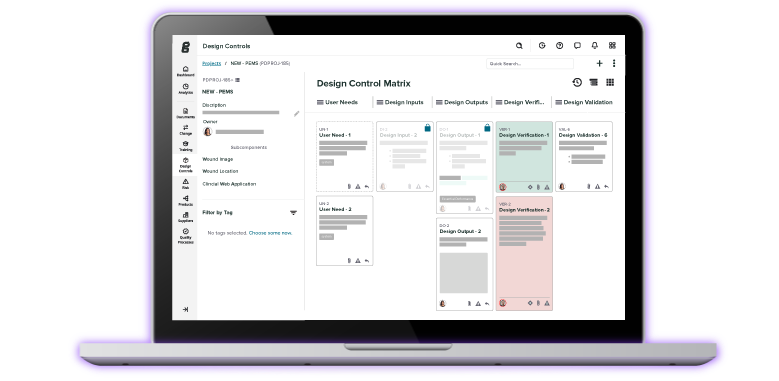
With Greenlight Guru, you can not only see the interconnectedness of your entire quality management system (QMS), you can demonstrate closed-loop traceability within the system. The connections between your risks and design controls have never been clearer than they are with Greenlight Guru.
Get a single, network view of all the relationships in your QMS. Get your free demo of Greenlight Guru today.
Looking for a design control solution to help you bring safer medical devices to market faster with less risk? Click here to take a quick tour of Greenlight Guru's Medical Device QMS software
Wade Schroeder is a Medical Device Guru at Greenlight Guru with a noticeable enjoyment of medical device product development processes. As an electrical engineer by trade, he began his career developing medical exam procedure chairs and later designing IVD devices. He has been a risk management enthusiast since the...
Related Posts
Do ISO 13485's Production Controls apply to SaMD?
Software Bill of Materials (SBOMs) & Cybersecurity in the Medical Device Industry
Cybersecurity for Medical Devices: Best Practices from Regulatory Standards
Get your free resource
How to Integrate Cybersecurity into Your Existing Medical Device Development Lifecycle